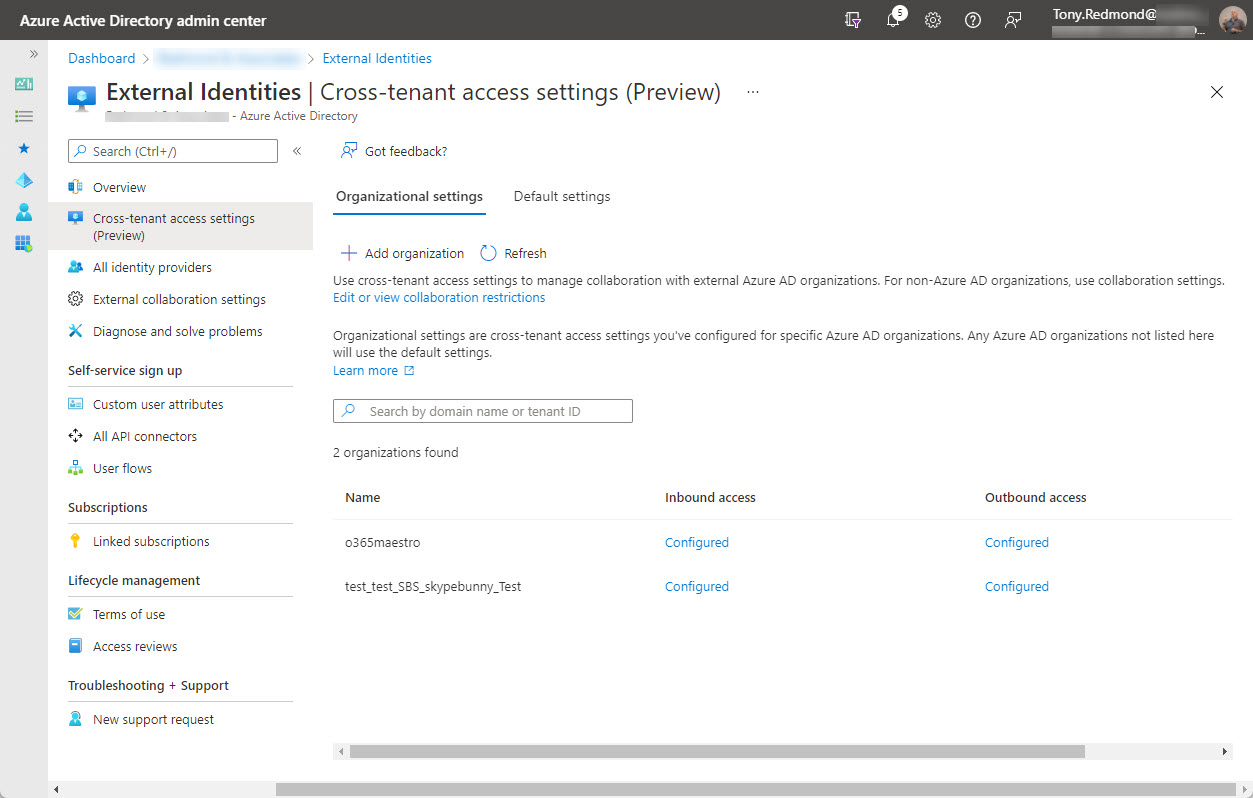
Azure AD conditional access policies can exert fine-grained control over the type of external users who can connect and what tenants they belong to. The new capability works especially well alongside Azure B2B Collaboration (guest users) and Azure B2B Direct Connect (used by Teams shared channels). It’s yet another way to impose control over who you allow to connect to your tenant.
On February 7, Microsoft announced the preview of Azure AD cross-tenant access, a new capability to allow users obtain credentials in their home tenant and use these credentials to access resources in other Microsoft 365 organizations. Microsoft Teams Connect (aka shared channels) is likely the first app to use cross-tenant access, with public preview of that feature expected in March 2022.
Some changes in the Microsoft Teams desktop and browser clients will allow users to decline guest invitations from other organizations, leave organizations, and hide organizations from Teams. Although leaving another organization has been a well-trodden path for several years, it’s required knowledge to find the right place to go. Having these options in Teams makes it much easier to manage a cluttered set of organizations.
Office 365 tenants using Entra ID external identities (like Entra ID B2B Collaboration guest accounts with apps like Teams) are moving to a monthly active users (MAU) billing model. The new model replaces the 1;5 ratio for Entra ID premium licenses used up to now. Microsoft allows tenants to have the first 50,000 unique external identities free of charge each month and bills for access thereafter. If you don’t already have an Azure subscription, you’ll need one to link to Entra ID. Linking the subscription should be an easy task, until it’s not…
Yammer networks configured in Microsoft 365 mode now support Azure B2B collaboration guest users. Which is nice, if it worked. But it doesn’t for me. Guest access worked for me during the testing phase but now that the feature has reached general availability, it won’t – using the same accounts. It’s odd. Yammer’s implementation of Azure B2B Collaboration has some other quirks too, all of which mean that it’s not very usable.
A new preview feature allows the resources available to an Azure AD guest account to be reassigned to another email address. It’s a nice feature, but Teams has some problems with it at present. On the upside, everything works great with SharePoint Online and Planner, and we’re sure that Microsoft will fix the problem with Teams soon.
Teams supports federated guest access for Gmail accounts using the identity provider framework of Azure B2B Collaboration. Office 365 tenants must first decide if they want Gmail accounts as guests in all or some teams before going down the federation route. Why Teams and not other Office 365 apps? It’s all to do with the endpoint used by the client to connect. If it can handle federation, all good. If not, it’s standard Azure B2B Collaboration.
Office 365 Informatiom Barriers allow tenants to erect communication firewalls between different groups. Teams supports Information Barriers, but currently has a problem adding new guest accounts to team memberships. An easy workaround exists, but debugging what’s going on is difficult because of the lack of clues.
When you impose a block on certain domains, you’d like to think that applications like Teams will respect that block. As it turns out, if you have some lingering guests in your Azure Active Directory, the B2B collaboration policy might not be as effective as you’d hope.
Microsoft has launched the preview of Google B2B Federation, which allows Google accounts to be used to access Azure AD apps. Quite how this will work out for apps that use guest user accounts is unknown at this point.