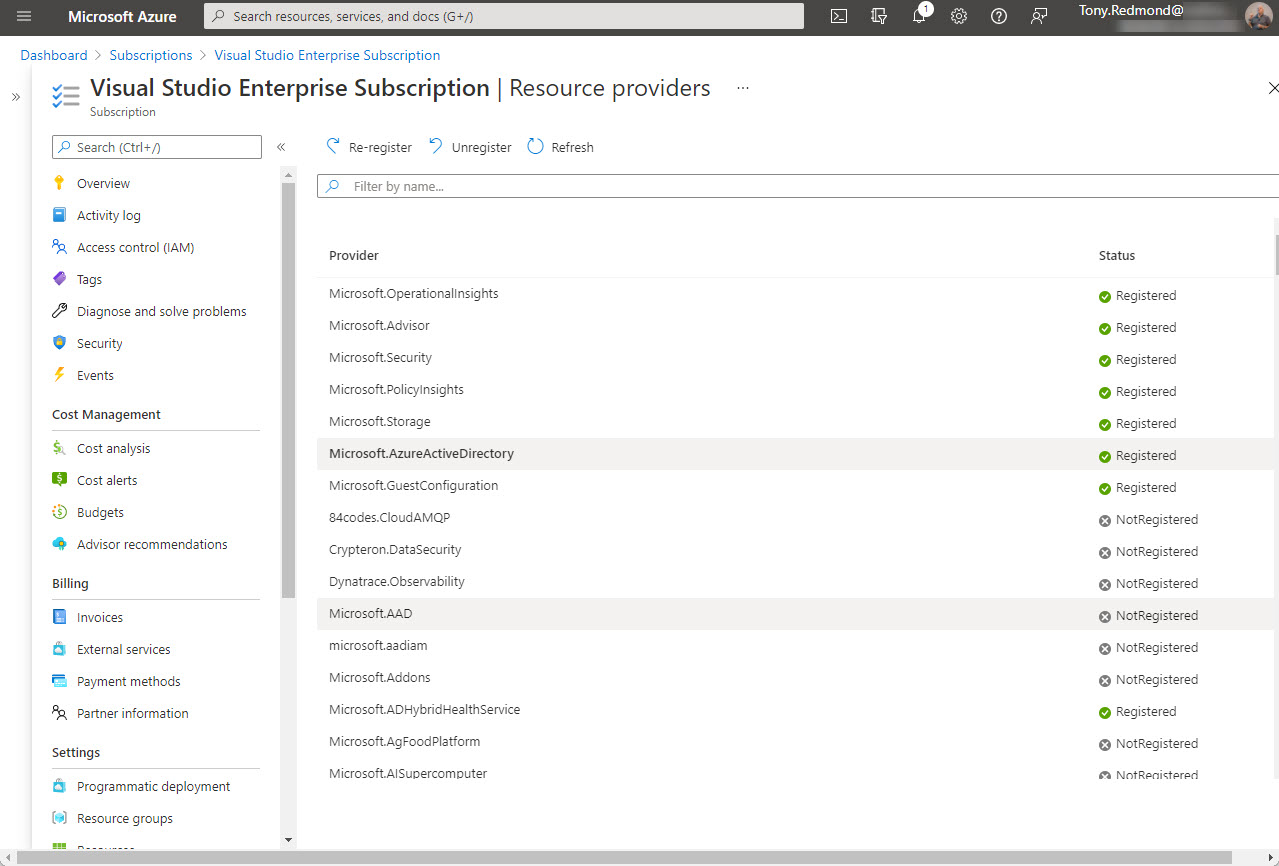
On January 10, Microsoft announced that the base Office 365 workloads support Continuous Access Evaluation (CAE) for critical Azure AD events like password changes or account deletions. Although you can take CAE even further with conditional access policies, giving Exchange Online, SharePoint Online, and Teams the ability to react to critical events in almost real-time is a very big thing indeed.
Microsoft Teams posts system messages to a team’s information pane to let people know about membership changes. You can’t stop Teams doing this because Microsoft doesn’t provide control over the system messages at the tenant or team level. You can obscure the names of new members by changing their display name, but maybe the best idea is not to add new members until the time is right.
Microsoft pushed out version 2.0.88.0 of the AAD Connect synchronization utility earlier this month. Unfortunately, the new software removes disabled on-premises user accounts from Azure AD, which means that on-premises shared mailboxes disappear for cloud users. Microsoft has released version 2.0.89.0 but maybe it’s better to go back to a version that you know works. At least until after the holidays.
Some changes in the Microsoft Teams desktop and browser clients will allow users to decline guest invitations from other organizations, leave organizations, and hide organizations from Teams. Although leaving another organization has been a well-trodden path for several years, it’s required knowledge to find the right place to go. Having these options in Teams makes it much easier to manage a cluttered set of organizations.
Azure AD has a history of outages which have caused problems for Microsoft 365 tenants over the years. Microsoft hopes to solve the problem with a backup authentication service that’s capable of keeping things going if the primary Azure AD service goes offline. Basically, the backup service has copies of successful authentications over the last three days which can be used to process authentication requests for most sessions when the primary service fails. It seems like a good idea.
A reader asked how to find when Azure AD accounts received certain licenses. As it turns out, this isn’t as simple as it seems. PowerShell can tell use when user accounts are enabled with service plans, but to get dates for licenses (products or SKUs), we need to go to the Graph API, and those dates aren’t quite there yet. In any case, it’s an interesting question which deserves some exploration to see if we can find an answer.
Office 365 tenants using Entra ID external identities (like Entra ID B2B Collaboration guest accounts with apps like Teams) are moving to a monthly active users (MAU) billing model. The new model replaces the 1;5 ratio for Entra ID premium licenses used up to now. Microsoft allows tenants to have the first 50,000 unique external identities free of charge each month and bills for access thereafter. If you don’t already have an Azure subscription, you’ll need one to link to Entra ID. Linking the subscription should be an easy task, until it’s not…
Understanding how to create effective queries using the Microsoft Graph APIs takes some work, especially with some of the more complex filters used to refine the data returned by the Graph. In this article, we look at how filters using lambda qualifiers work and explore some examples of these qualifiers in use.
Azure AD administrators should be able to assign a reserved alias to a new group. At least, that’s what the documentation says. As it turns out, this isn’t strictly true as there are places where administrative interfaces (GUI and PowerShell) block any attempt to use reserved aliases. Does this matter? Probably not, unless you like consistency… which we do!
In this post, we describe how to use PowerShell to remove a single service plan from Microsoft 365 licenses using PowerShell. The script can remove any service plan from any SKU (license) in a tenant. You might want to do this to disable access to an obsolete feature (like Sway) or to prevent access to a new feature until the organization is ready to support user activity.
In October 2021, Microsoft will enable the Azure AD email one-time passcode identity provider in tenants. SharePoint Online and OneDrive for Business will use the provider to control access for external people to its resources. The net effect is that Azure AD will create guest accounts for external sharing recipients. Even though guest accounts need to be managed, there’s lots of good reasons to use guest accounts, as we describe here.
Controlling the creation of Microsoft 365 Groups might seem complex, but it’s not as complicated as it might seem. Make sure Azure AD allows group creation, and then you can either allow everyone to create new groups or restrict the right to a limited set of accounts (a capability requiring Azure AD Premium licenses). And don’t forget OWA, because it’s got its own mailbox policy with a group creation setting. All good, clean, honest fun.
Microsoft has updated the creation settings for security groups and Microsoft 365 groups in the Azure AD admin center. The changes impose consistency over administrator creation of these groups and probably won’t affect tenants, but it’s good to check. The change makes us ponder why Microsoft doesn’t improve the GUI for other group controls, like those controlling who can create new Microsoft 365 Groups.
The preview of a new app governance add-on for Microsoft Client App Security gives Office 365 administrators insight into Graph-based apps. The add-on depends on information gathered from Azure AD and MCAS to generate insights about apps and their usage, including highlighting apps which are overprivileged or highly privileged. Although you can do some of the auditing yourself, the add-on makes it easier. It’s a preview, so some glitches are present.
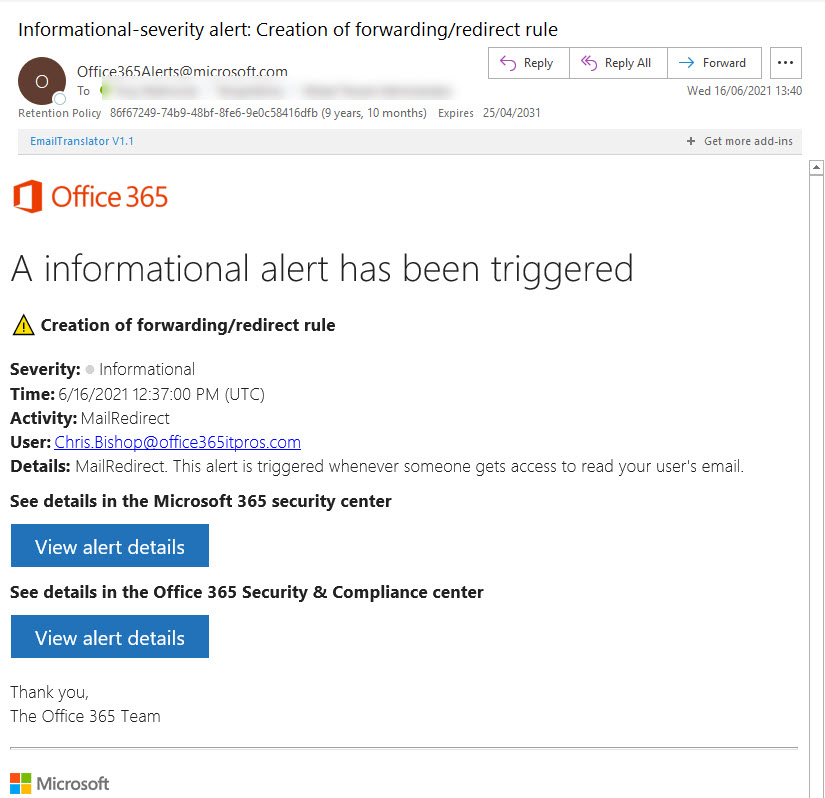
The need to remove basic authentication from Exchange Online is underlined by a June 14 report from the Microsoft Threat Intelligence Center pointing to how attackers compromise mailboxes using antiquated protocols like POP3 and IMAP4 to connect to accounts which don’t use MFA. After accounts are penetrated, the attackers plant inbox rules to forward copies of interesting messages and use the information received to plan and execute business email compromise attacks. Tenant administrators still have some work to do to secure Exchange Online and Azure AD…
A preview for Sensitivity Labels show how they can use Azure AD authentication contexts and conditional access policies to protect SharePoint Online sites. Although you can link conditional access policies to sites with PowerShell, it’s a lot easier to make the connection through sensitivity labels. Any SharePoint Online site which receives a label configured with an authentication context automatically invokes the associated conditional access policy to protect its contents.
Finding out which Azure AD accounts have licenses (service plans) for different applications isn’t difficult. You can do it with either PowerShell or the Microsoft Graph API. This article explains how to use PowerShell (and the equivalent Graph API call) to find accounts which have a certain license (service plan) enabled or disabled. Once you know how to navigate license data in Azure AD accounts, you can take the code and adapt it for different purposes.
Anyone writing PowerShell code against Azure Active Directory probably uses the Azure AD module. In June 2022, Microsoft will deprecate the API underpinning the Azure AD module. Tenants who want to use PowerShell to create scripts to automate administrative processes will need to move to Graph API calls or use the Microsoft Graph PowerShell SDK. Either way, there’s a bunch of work to do to upgrade scripts.
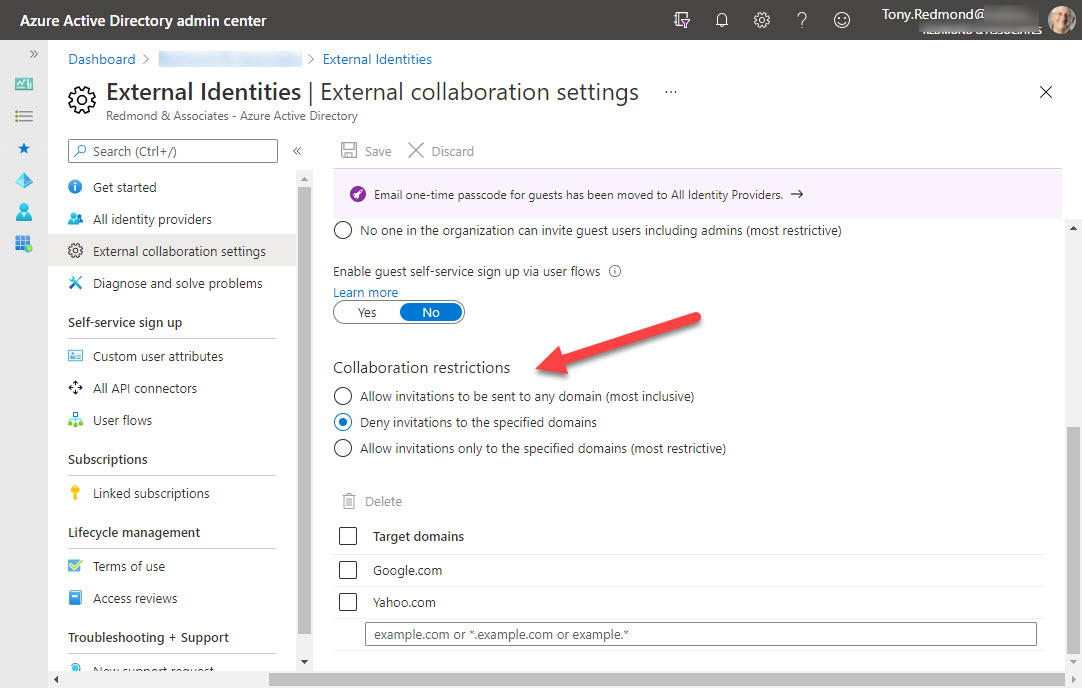
Blocking domains through the Azure AD B2B collaboration policy stops group owners adding new guest accounts from certain domains. It does nothing about existing guests from those domains. Fortunately, it’s relatively easy to check the guest membership of Groups and Teams to find guests from the blocked domains. And once you know those problem guests, you can decide what to do up to and including removing guest accounts from the tenant.
Without warning (for security reasons), Microsoft stopped the Exchange Online Set-User cmdlet being able to update the work and mobile numbers for Azure AD accounts. We don’t know what kind of security concerns caused Microsoft to take this action, but it might be associated with administrative roles. In any case, this disappointing example of how to communicate with customers might end up with people having to update some PowerShell scripts – and no one likes unexpected work.
Azure B2B collaboration is used by Microsoft 365 Groups-based apps like Teams, Planner, and Yammer to control the creation of new guest accounts. You can update settings in the Azure AD portal to stop new accounts from specific domains or restrict guests to a list of known domains. But before you go ahead and update the settings, it’s a good idea to know where existing guest accounts come from. It’s easy to create a report with PowerShell. The next step might be to remove guests from offending domains.
Office 365 administrators can update Azure AD guest accounts with photos. Guests can do the job themselves using three PowerShell commands. Other approaches work too, but this is the easiest and quickest method to do the job, especially if you have guest accounts in multiple tenants.
Organizations can choose to control updates of user photos by policy in their Microsoft 365 tenants or allow users to go ahead and use any image they like. In this article, we explore the value of having a user photo for every Office 365 account (and Teams and Groups too) and the choices organizations must make when they decide whether to control user-driven updates.
Azure AD holds information about managers and their direct reports. It’s easy for that data to go out of date, so we create a report to tell us who are the managers and how many direct reports they have. Azure AD has some cmdlets to retrieve information about managers and direct reports, but as it turns out, the older Get-User cmdlet is the best way to proceed.
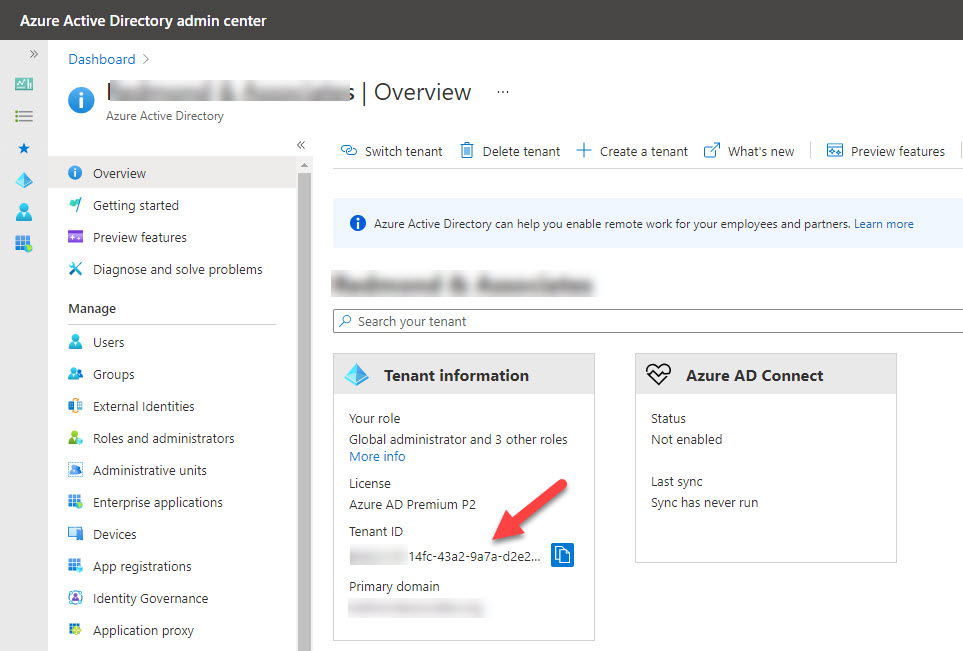
Every Microsoft 365 tenant has a tenant identifier. Sometimes you need to know what the identifier is, so here are several options to find it from PowerShell to the Azure AD portal to an external service. Tenant identifiers are public and need to be, otherwise apps wouldn’t be able to find the data they want.
A new preview feature allows the resources available to an Azure AD guest account to be reassigned to another email address. It’s a nice feature, but Teams has some problems with it at present. On the upside, everything works great with SharePoint Online and Planner, and we’re sure that Microsoft will fix the problem with Teams soon.
The OneDrive sync client is an important Microsoft 365 component which underpins features like autosave and coauthoring of Office documents. During the March 15 Azure AD outage, the client had a meltdown and removed all the local copies of files stored in a SharePoint Online folder, seemingly because it couldn’t authenticate. The problem was easily fixed, but it’s a bad example of handling what could be a transient authentication issue.
The Office 365 audit log is packed full of information about what happens inside workloads. New events show up all the time. The question is how to understand what actions these events relate to. We outline a simple procedure to discover the presence of new audit events and dive into the investigation of an event called Consent to application, which is pretty important in the context of recent high-profile attacks.
You can create an Azure AD Access Review for all guests in teams and groups in your tenant and then see what’s happening with the Graph API. In this case, we use PowerShell with the API to grab the access review data and create a report about the overall status of the review in a tenant.
Exchange dynamic distribution lists allow messages to be sent to sets of recipients determined by a query against the directory. A custom filter is a powerful way to find the right set of recipients. In this case, we want to find mailboxes with certain job titles whose Azure AD accounts are not blocked for sign-in. Here’s how to create the filter, make sure it works, and create the DDL.
A new Graph API and the Teams AadSync process improve how Teams synchronizes group membership information with Azure AD. The older background sync process was tied to the Teams client and didn’t work so well in practice, especially when scaled up. Things look good for the new mechanism.
Many Microsoft 365 features depend on accurate user account data in Entra ID (Azure AD). Here’s how to use PowerShell to track down accounts with important missing properties. Once you know which accounts need to be updated, it’s easy to insert the missing properties. Boring, but easy…
Exchange Online Dynamic Distribution Lists are a powerful way to address changeable groups of recipients. The query against the directory is the big thing to get right, but you’ve also got to make sure that the directory data is accurate and reliable. Once you’ve got a good directory, it’s easy to create dynamic distribution lists which are easy to use and never go out of date.
Over time, you might join several Office 365 tenants as a guest. Some of those Azure AD guest accounts probably won’t be needed forever and you want to clean them up. This is easy for individuals to do through their MyAccount page, which might just be a page that they never knew existed.
Microsoft’s FY21 Q3 results told us that Teams now has 115 million users, a 53% uptick since April. Office 365 keeps on growing in numbers, revenue, and profit. While growth might be slowing, there’s still a ton of accounts to be moved to the cloud, where they’ll probably end up as Teams users.
The Active Directory schema includes a drink attribute. This didn’t make the transition to Azure AD, but you can use one of the custom attributes to make drink show up on Microsoft 365 profile cards. This might not seem like a good use of your time, but it’s actually an illustration of how to put the Microsoft Graph Explorer tool to good use.
Microsoft announced that the Azure AD Sign-in Activity Report for end users is now generally available. Good progress has been made since the preview, but some problems still persist. It’s fair to ask end users to review their sign-in activity, but to have a chance of catching problems, the data you ask people to review must be understandable by them, and sometimes the data in this report isn’t.
You can apply an Office 365 Sensitivity Label to control different aspects of Groups, Teams, and Sites. One of the settings controls whether guest users are allowed in group membership. We explain how to use PowerShell to search groups assigned a label to block guest access for existing guests, just in case you want to remove them.
Microsoft 365 Business Premium customers will benefit from the provision of Azure Active Directory P1 Premium licenses. All good, but what about the Office 365 E3 tenants who pay the same monthly fee? Many enterprise tenants could use the features licensed by Azure Active Directory Premium P1, but they’ll have to pay $6/user/month to get the same benefit.
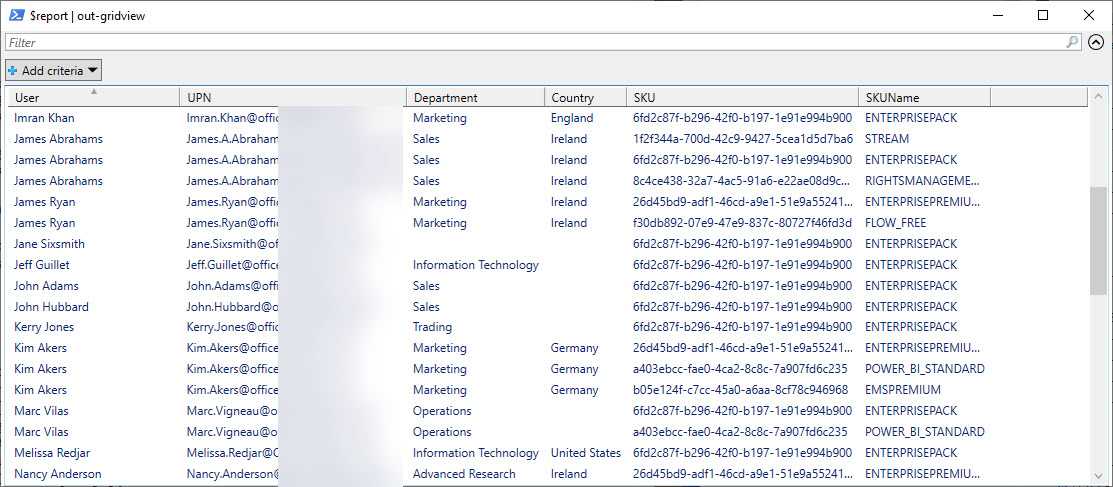
Office 365 licenses can seem complex, especially when you descend to the level of multi-product license plans. PowerShell makes it easy to generate a quick and simple report of who’s been assigned which license. And best of all, because the code is PowerShell, you can amend it to your heart’s content.