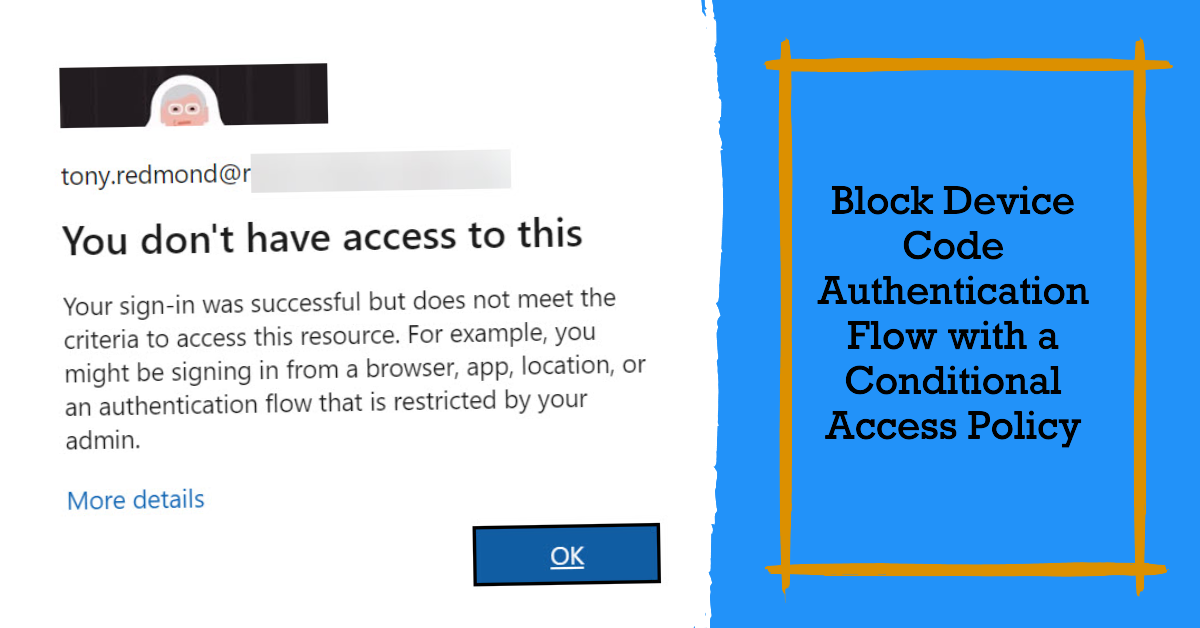
This article describes the process of blocking device code authentication requests against Entra ID with a preview feature for conditional access policies. It’s a good idea to tighten tenant security by removing device code authentication unless a clearly-defined need exists for apps to authenticate using this method. I suspect that most tenants will find that they can happily do without device code authentication.
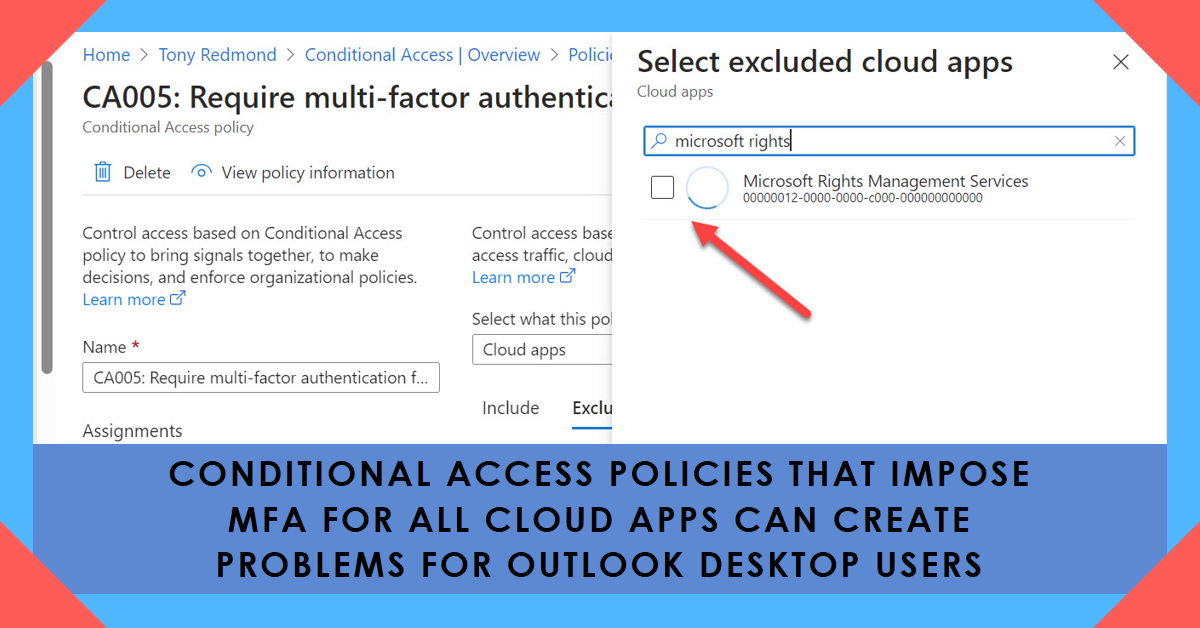
If conditional access policies impose MFA for all cloud apps, it gives external users a problem when they use Outlook desktop to read protected email. The issue is because Outlook can’t obtain a use license to decrypt the content because it can’t satisfy the MFA challenge. It’s an example of how two good parts of the Microsoft 365 ecosystem clash.
Conditional access policies control access to Entra ID connections. Policies should have exclusions for breakglass accounts, but sometimes this doesn’t happen. This article explains how to use cmdlets from the Microsoft Graph PowerShell SDK to check conditional access policies and update policies with exclusions where necessary.
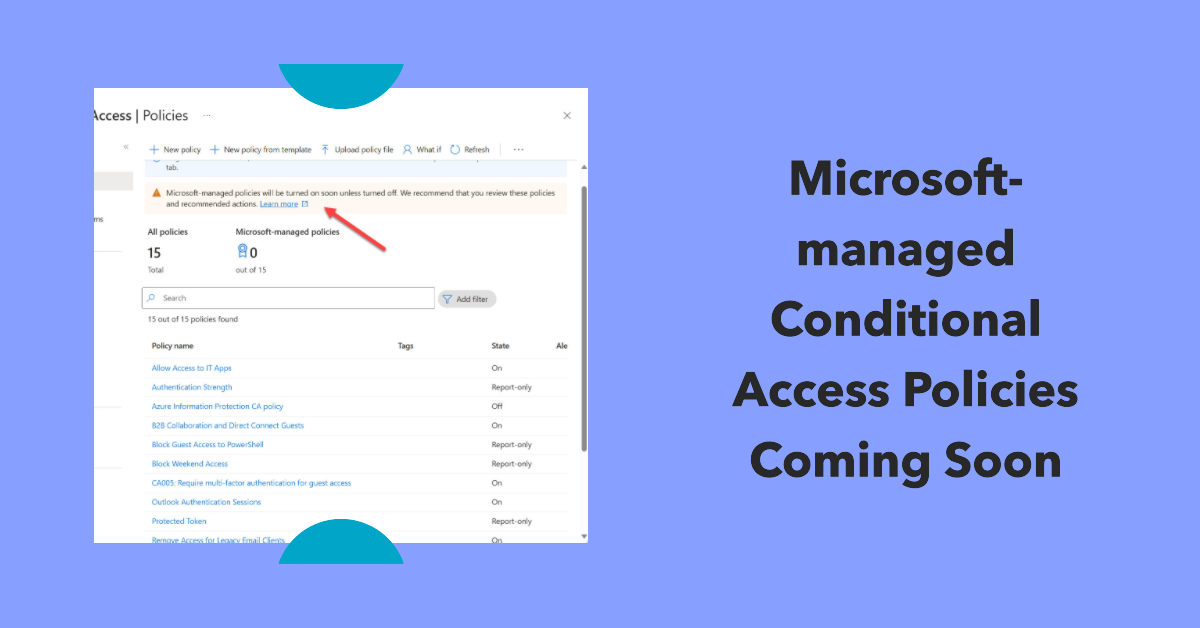
On November 6, Microsoft announced that they will deploy Microsoft-managed conditional access policies to eligible tenants. A conditional access policy controls the connections users want to make to apps or data by setting conditions. In this case, the Microsoft policies will require MFA before access is granted to apps like administrative portals.
Microsoft has decided to push the final deprecation of client access rules to September 2024. However, only rules that can’t be migrated can be used until then. All other client access rules will stop working in September 2023. Microsoft isn’t clear about what technical limitations might allow rules to work for the extra year, nor do they say how tenants can check except by “opening a support ticket.” Although it’s good to move to conditional access policies, Microsoft really could communicate better.
The first app in a new community project called IdPowerToys helps Microsoft 365 tenants to document conditional access policy settings in PowerPoint. The information used to document the CA policies is extracted (manually or automatically) from Azure AD, analyzed, and output as a PowerPoint presentation. It’s a nice way to see what CA policies exist in a Microsoft 365 tenant and helpful if you want to rationalize the set of policies in use.
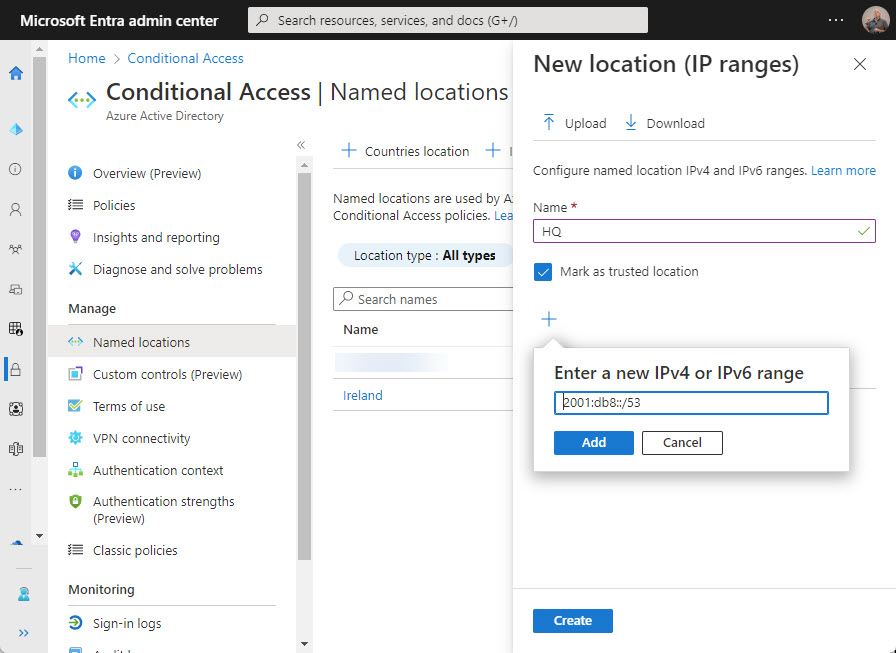
Microsoft plans to support IPv6 connectivity for Azure AD starting on March 31, 2023. The change creates specific requirements for conditional access policies that use named locations to allow or block connections. Administrators will have to add new IPv6 address ranges to named locations to allow users to continue to connect. Apart from that, it’s a matter of making sure that any reporting, analysis, or SIEM applications can deal with the new IPv6 data.
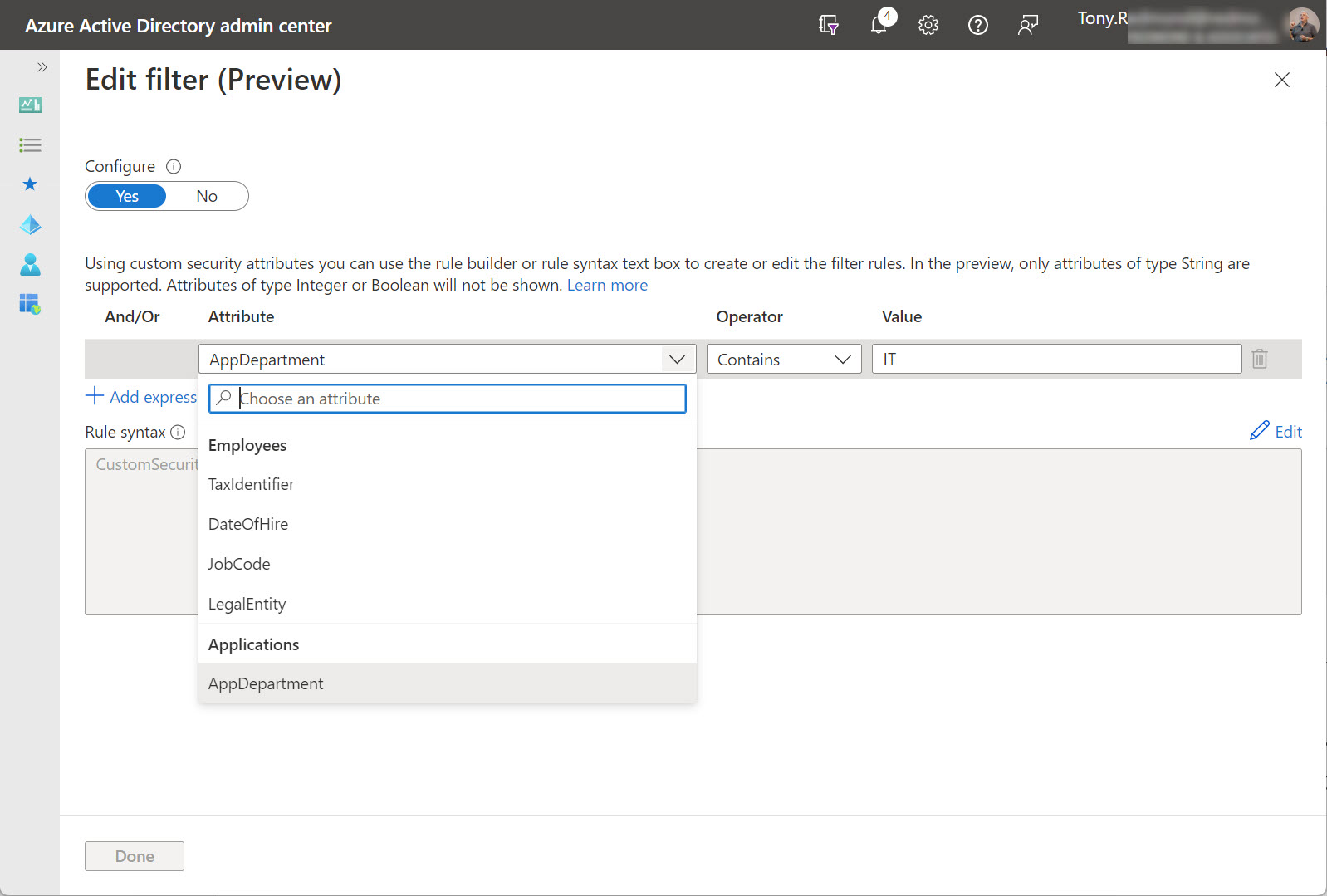
Azure AD conditional access policies can now use an app filter based on custom security attributes to restrict access to specific apps. It’s a neat idea that should be popular in larger enterprises where the need exists to manage large numbers of apps. In other news, the Graph X-Ray tool is available in the Windows Store and a neat cmd.ms tool is available to provide shortcuts to Microsoft 365 sites.
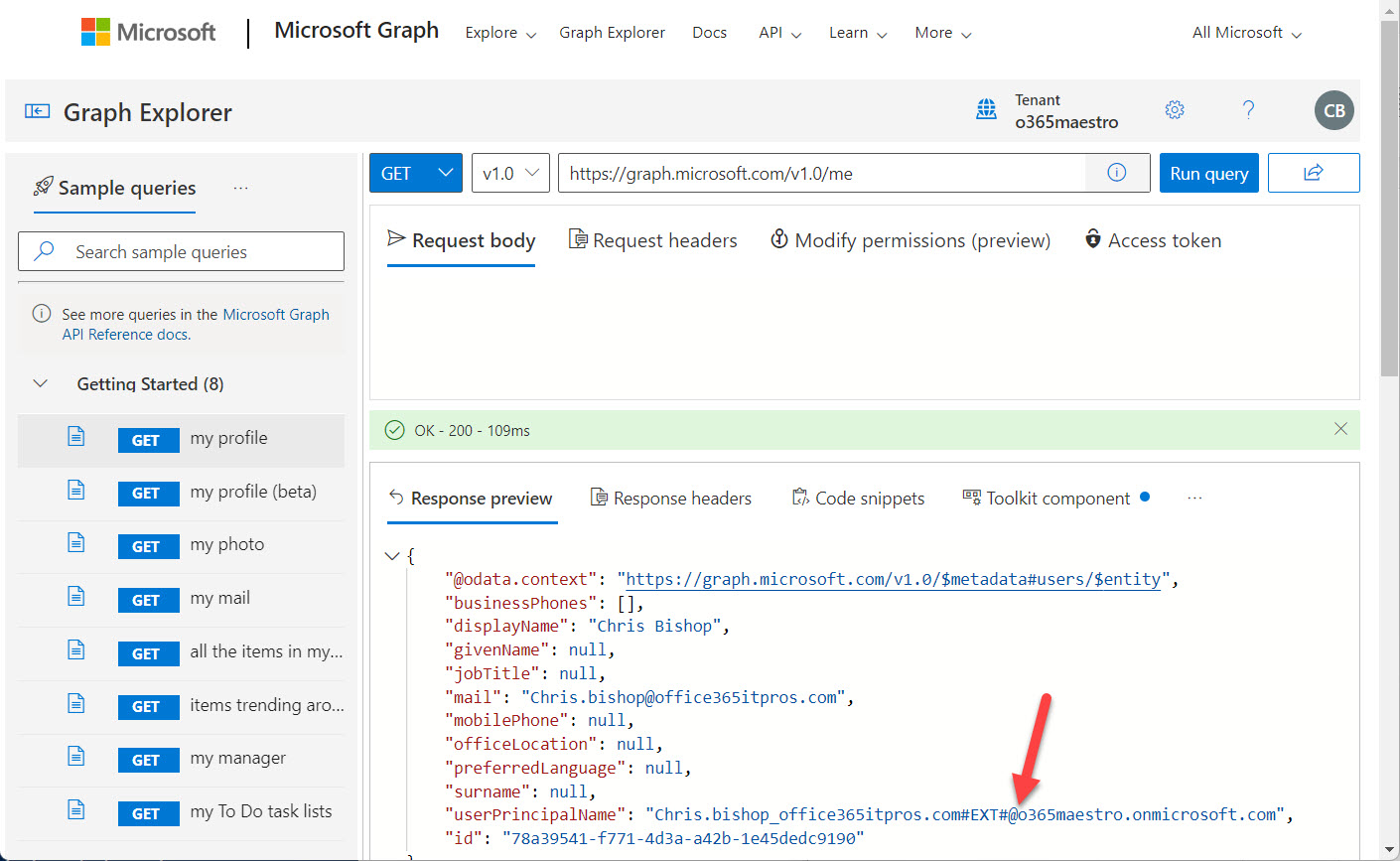
A little known fact about the Graph Explorer utility is that you can use it to sign into a tenant using a guest access. This might or might not be a good idea, but if you don’t want people to do this, it’s easy to block guest access by either disabling user access to the app (crude) or using a Conditional Access policy (much nicer).
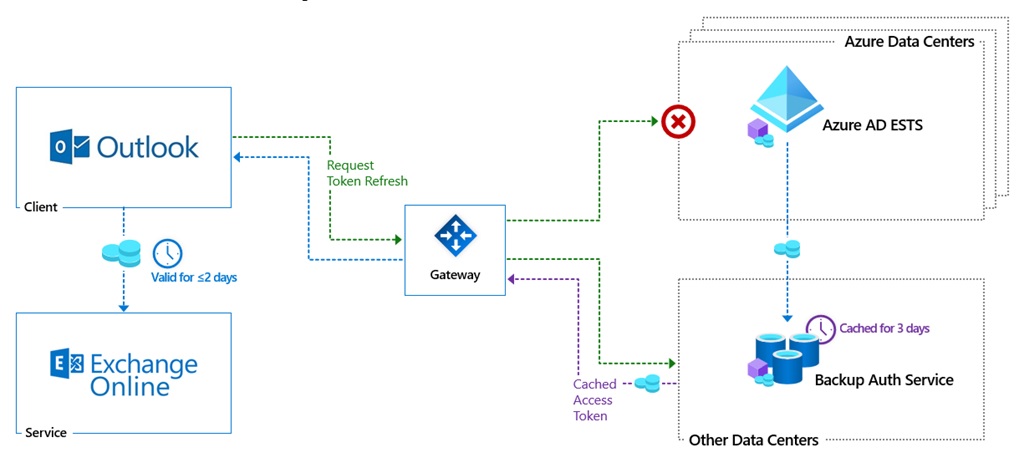
Azure AD has a history of outages which have caused problems for Microsoft 365 tenants over the years. Microsoft hopes to solve the problem with a backup authentication service that’s capable of keeping things going if the primary Azure AD service goes offline. Basically, the backup service has copies of successful authentications over the last three days which can be used to process authentication requests for most sessions when the primary service fails. It seems like a good idea.
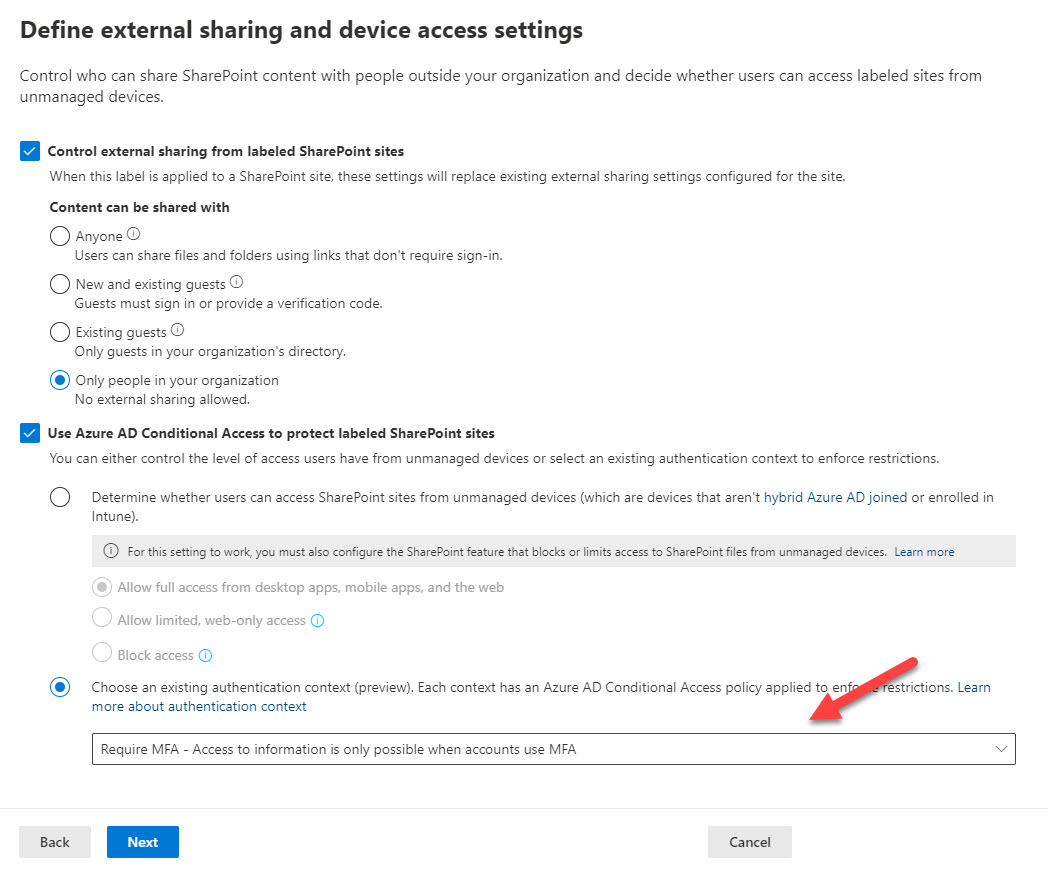
A preview for Sensitivity Labels show how they can use Azure AD authentication contexts and conditional access policies to protect SharePoint Online sites. Although you can link conditional access policies to sites with PowerShell, it’s a lot easier to make the connection through sensitivity labels. Any SharePoint Online site which receives a label configured with an authentication context automatically invokes the associated conditional access policy to protect its contents.
Exchange Online protocol authentication policies control what protocols a user can connect to mailboxes with, but it would be much better if we didn’t have to worry about some old and insecure protocols. Azure Active Directory gives Office 365 tenants the chance to clamp down on IMAP4 and POP3 connections and close off some of the holes that attackers try to exploit. Microsoft says that this can lead to a 67% reduction in account compromises, so that’s a good thing.