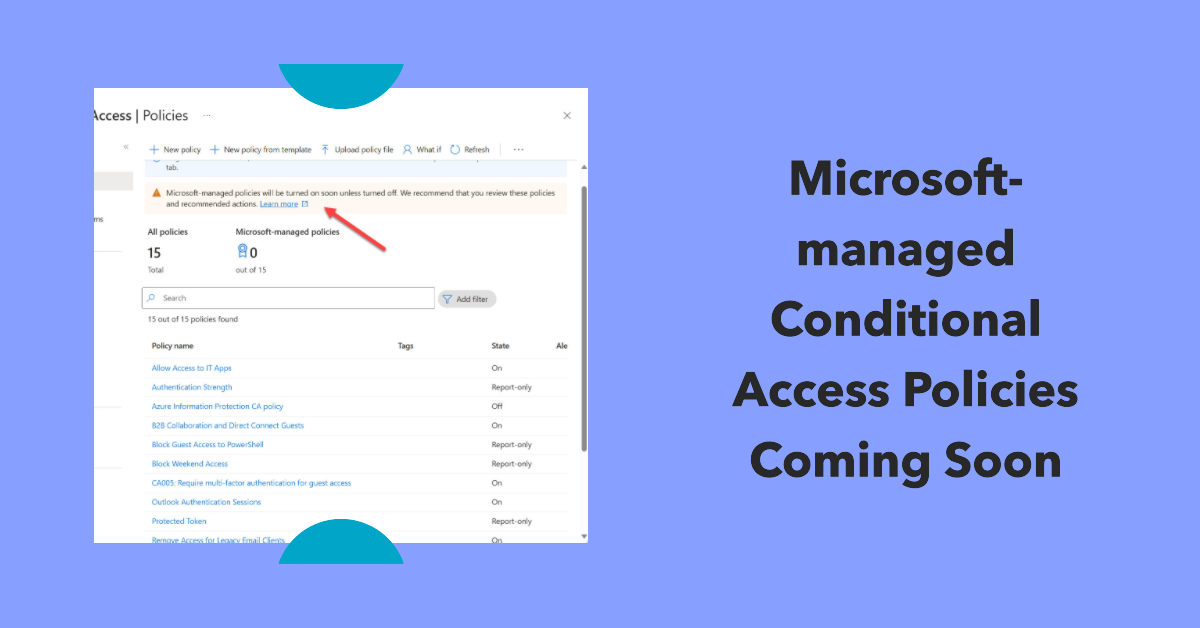
On November 6, Microsoft announced that they will deploy Microsoft-managed conditional access policies to eligible tenants. A conditional access policy controls the connections users want to make to apps or data by setting conditions. In this case, the Microsoft policies will require MFA before access is granted to apps like administrative portals.
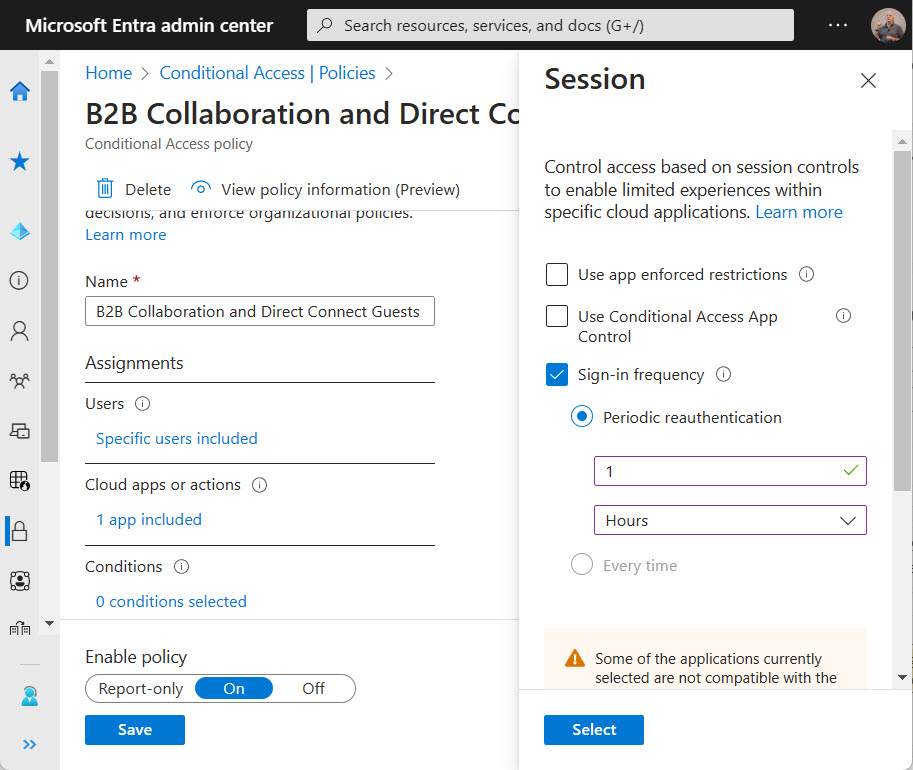
The Azure AD sign-in frequency controls how often accounts must reauthenticate. Setting an unreasonably short value makes it more difficult for people to work because Azure AD constantly nags for credentials, including MFA challenges. I experienced the effect of such a policy last week and it wasn’t nice. Security policies need to be practical and pragmatic as well as effective.
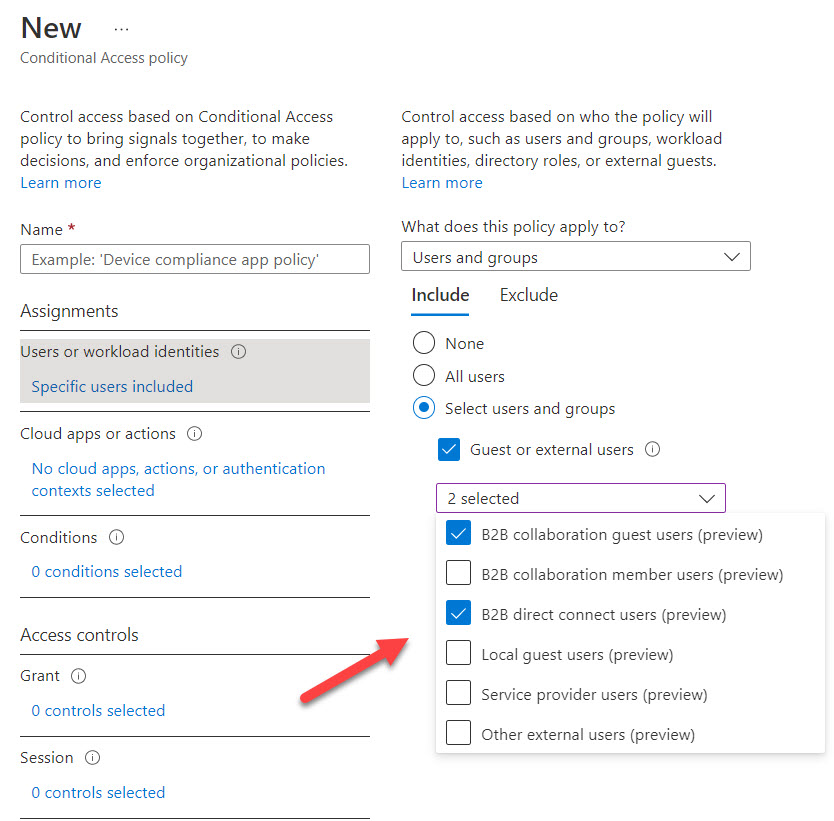
Azure AD conditional access policies can exert fine-grained control over the type of external users who can connect and what tenants they belong to. The new capability works especially well alongside Azure B2B Collaboration (guest users) and Azure B2B Direct Connect (used by Teams shared channels). It’s yet another way to impose control over who you allow to connect to your tenant.
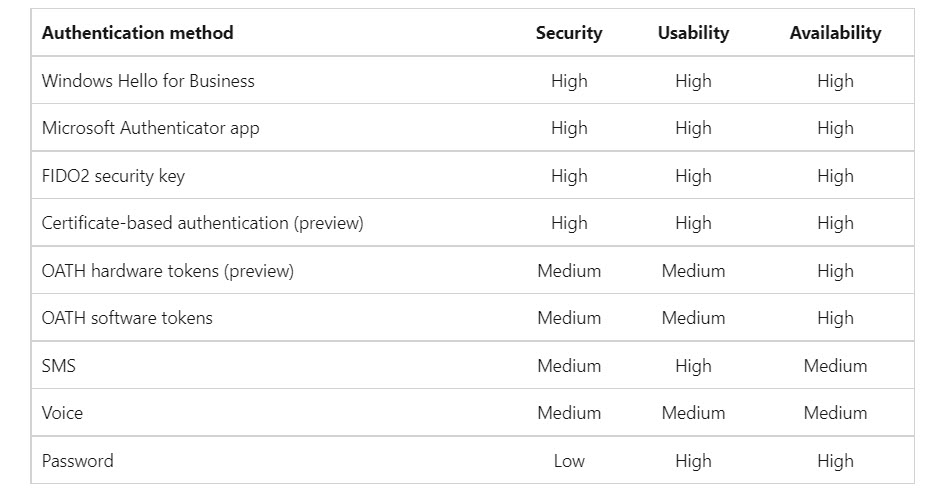
A new setting for Azure AD conditional access policies allows organizations to dictate the authentication strength of accepted connections. This is part of a Microsoft effort to move MFA-enabled Azure AD accounts away from the relatively insecure SMS-based challenges to methods that are less susceptible to attack.