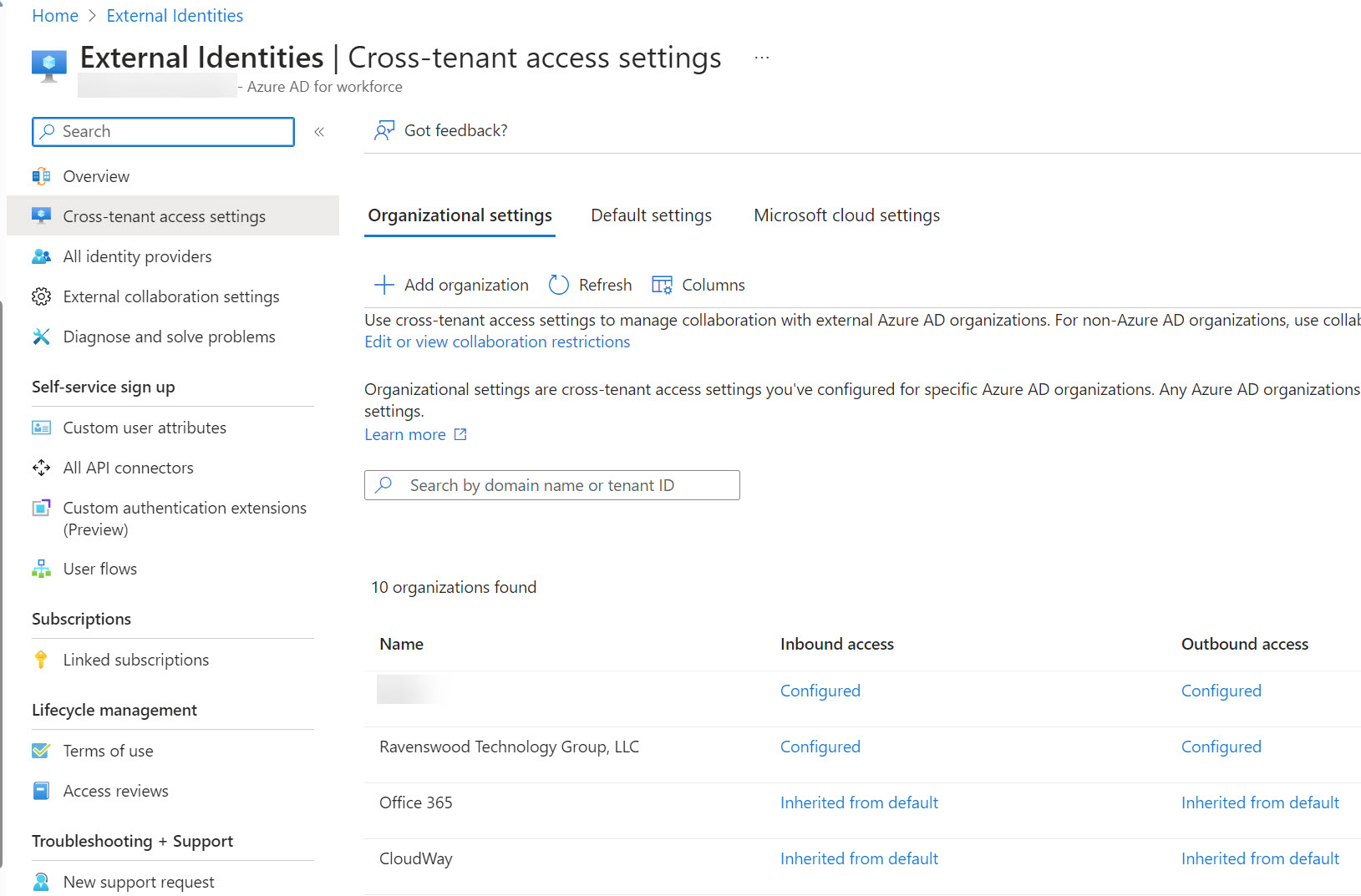
Microsoft announced three changes to Entra ID cross-tenant access settings that will improve how the settings work for large enterprise tenants in particular. One of the changes improves the blocking of Entra ID B2B Collaboration invitations extended to allow guest users access resources in a tenant. When Entra ID evaluates whether it should issue an invitation, it now takes the blocklist (if set) in the B2B collaboration policy and cross-tenant access settings into account. It’s the way things should have worked from the start.
SharePoint Online is embracing Azure AD more closely by forcing new tenants to use the integration between the two Microsoft 365 components. In addition, site sharing will use the Azure AD invitation mechanism instead of SharePoint’s own code. The changes make a lot of sense and shouldn’t cause much disruption for tenants. It’s a good reminder to check the relevant policies that control external access via Azure B2B Collaboration.
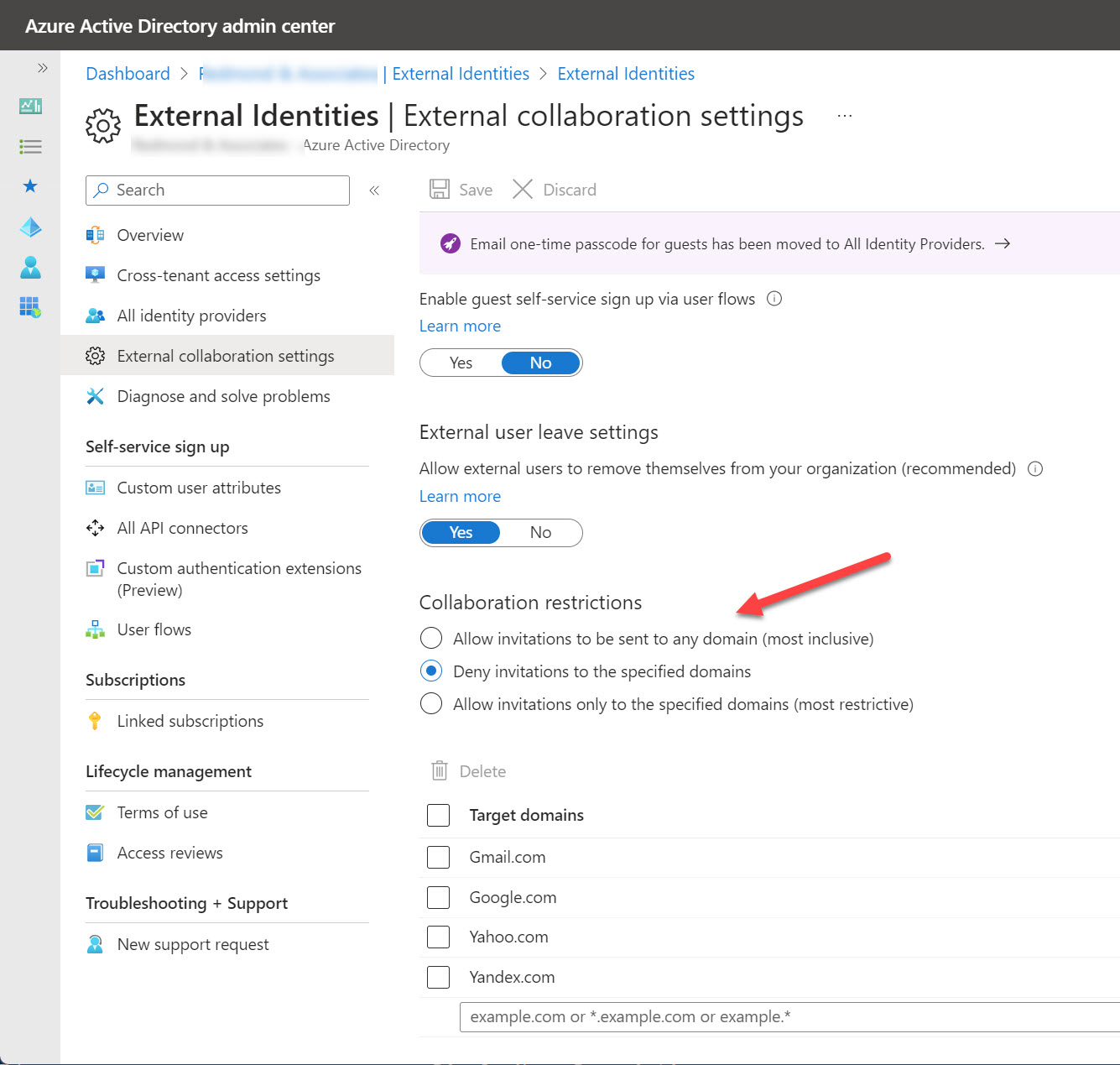
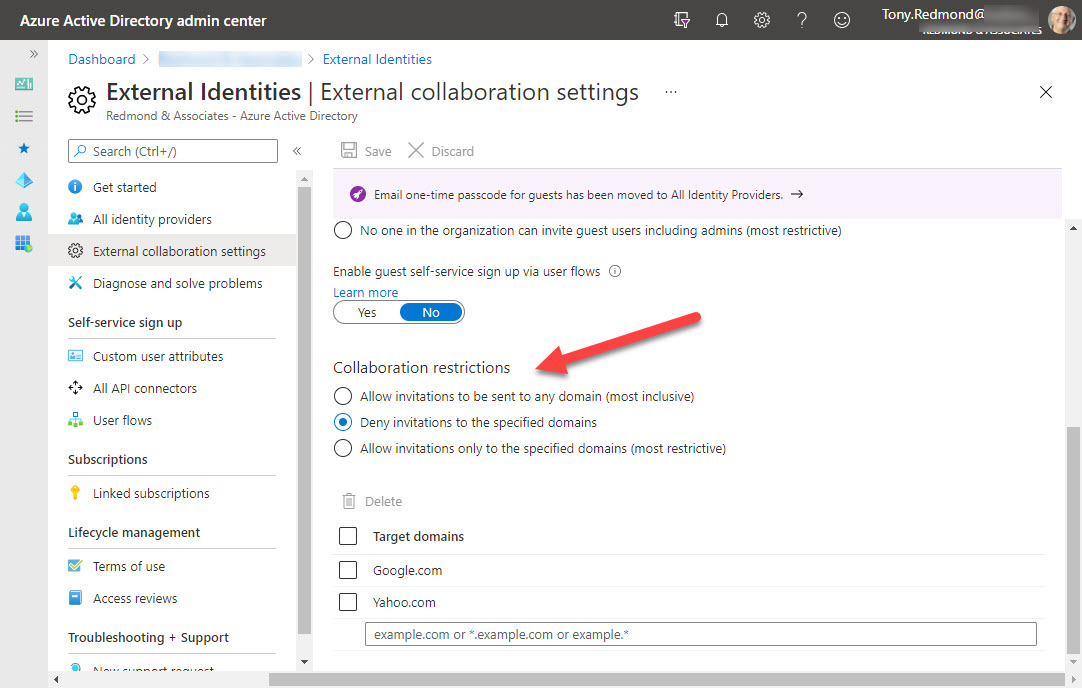
Blocking domains through the Azure AD B2B collaboration policy stops group owners adding new guest accounts from certain domains. It does nothing about existing guests from those domains. Fortunately, it’s relatively easy to check the guest membership of Groups and Teams to find guests from the blocked domains. And once you know those problem guests, you can decide what to do up to and including removing guest accounts from the tenant.
Azure B2B collaboration is used by Microsoft 365 Groups-based apps like Teams, Planner, and Yammer to control the creation of new guest accounts. You can update settings in the Azure AD portal to stop new accounts from specific domains or restrict guests to a list of known domains. But before you go ahead and update the settings, it’s a good idea to know where existing guest accounts come from. It’s easy to create a report with PowerShell. The next step might be to remove guests from offending domains.